Security Information and Event Management solutions (SIEM)

Security Information and Event Management (SIEM) is a comprehensive approach to managing an organization’s security posture by combining information from various sources, detecting security events, and providing real-time analysis of security alerts. SIEM solutions help organizations monitor and respond to potential cybersecurity threats, as well as comply with regulatory requirements.
Log Collection and Aggregation: SIEM solutions collect logs and data from various sources across an organization’s network, including firewalls, intrusion detection/prevention systems, servers, endpoints, and applications. These logs are aggregated into a centralized repository for analysis.
Real-time Event Correlation: SIEM tools analyze and correlate events from different sources to identify patterns, anomalies, and potential security incidents. Correlation helps distinguish between normal network activities and potential threats.
Security Alerts and Notifications: When the SIEM system detects suspicious or anomalous behavior, it generates security alerts and notifications. These alerts are sent to security analysts or administrators in real-time, allowing for rapid response.
Threat Detection and Incident Response: SIEM solutions help organizations detect security threats such as unauthorized access, malware infections, data breaches, and insider threats. By providing real-time alerts, SIEM assists in incident response and mitigation.
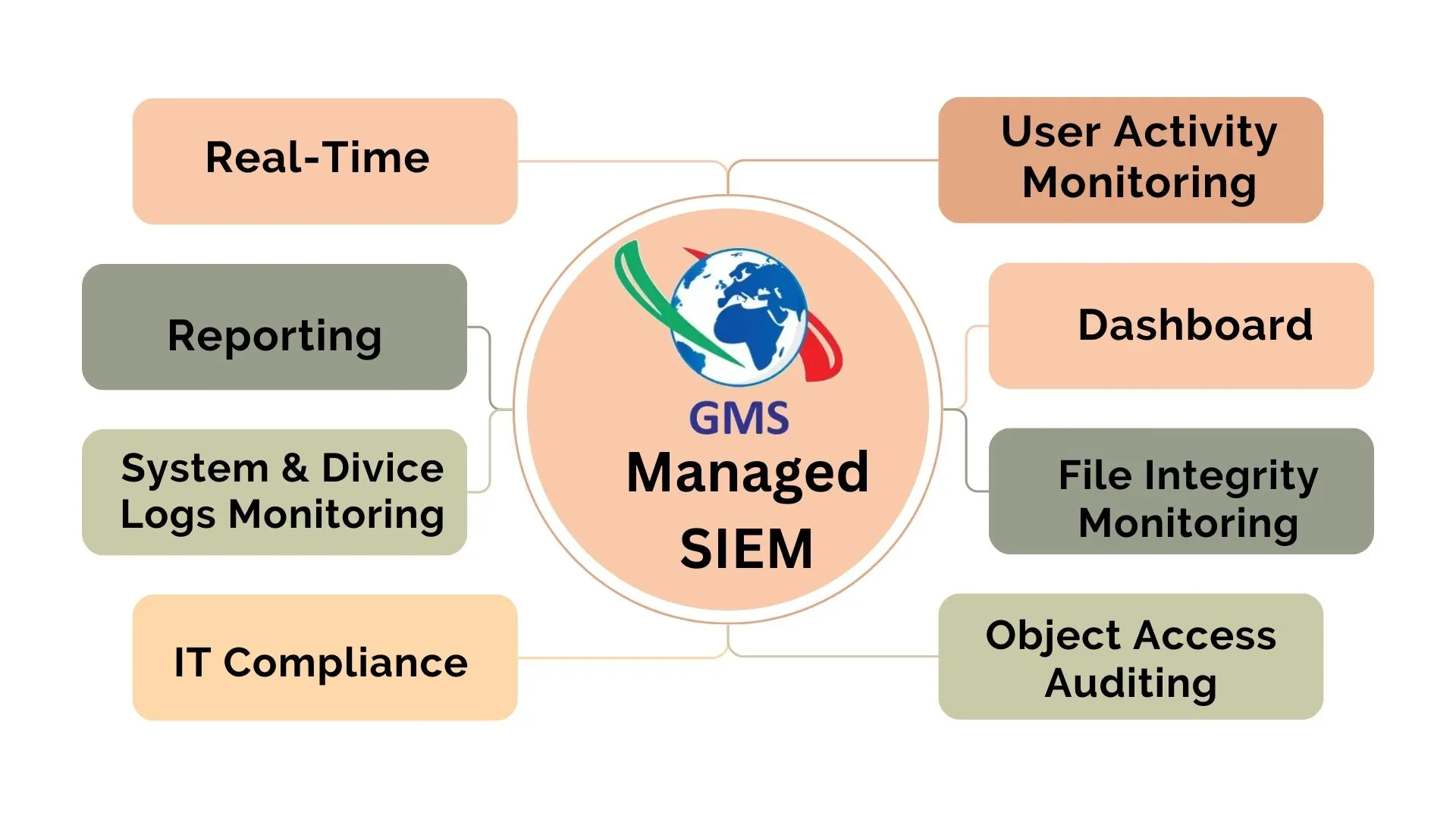
User and Entity Behavior Analytics (UEBA): SIEM solutions can use machine learning and behavior analytics to identify unusual behavior patterns exhibited by users and entities on the network. This helps detect insider threats and compromised accounts.
Compliance Management: SIEM solutions assist organizations in meeting regulatory compliance requirements by collecting and analyzing data to demonstrate adherence to industry standards and regulations.
Forensics and Investigation: SIEM tools provide forensic capabilities that allow security teams to investigate and analyze incidents after they occur. This helps in understanding the nature of the attack, identifying the attack vector, and preventing future incidents.
Data Visualization and Reporting: SIEM solutions often offer customizable dashboards and reports that provide visual insights into network security and compliance status. These reports can be used for auditing, management, and communication purposes.
Integration with Security Tools: SIEM solutions can integrate with other security tools, such as intrusion detection systems (IDS), intrusion prevention systems (IPS), antivirus software, and threat intelligence feeds. This integration enhances the SIEM’s ability to detect and respond to threats.
Compliance Reporting: SIEM tools assist organizations in generating compliance reports required for audits and regulatory purposes. These reports demonstrate the organization’s adherence to security standards and policies.
Centralized Management: SIEM solutions provide a centralized platform for managing security-related data, alerts, and incidents. This streamlines the monitoring and response process, especially in complex network environments.
In summary, Security Information and Event Management (SIEM) solutions offer a centralized approach to monitoring, detecting, and responding to security events within an organization’s IT environment. By providing real-time analysis, correlation of security events, and comprehensive reporting, SIEM tools help organizations enhance their cybersecurity posture and effectively manage potential threats.
